“With Cisco ASA with FirePOWER Services, you consolidate multiple security layers in a single platform, eliminating the cost of buying and managing multiple solutions. This integrated approach combines best-in-class security technology with multilayer protection integrated in a single device that is less costly than piecemeal security solutions.â€
For more information, see Cisco’s product description: http://www.cisco.com/c/dam/en/us/products/collateral/security/asa-firepower-services/at-a-glance-c45-732426.pdf
Malware Patrol provides threat data compatible with Cisco ASA FirePOWER security intelligence feeds. There are three types of feeds that can be applied:
- IP addresses: includes IP addresses of malware C&Cs as well as those resolved from malware and ransomware DGAs.
- URLs: includes partial URLs used by malware and ransomware to contact command and control systems and drop zones.
- Domains: includes registered active domains generated via DGAs for malware and ransomware.
You can follow these simple steps to configure your Cisco ASA FirePOWER to filter malicious IPs and protect the internal network, computers and users from getting infected by malware. The same procedure can be followed to filter URLs and domains.
1) Log in to Cisco FirePOWER Management Center.
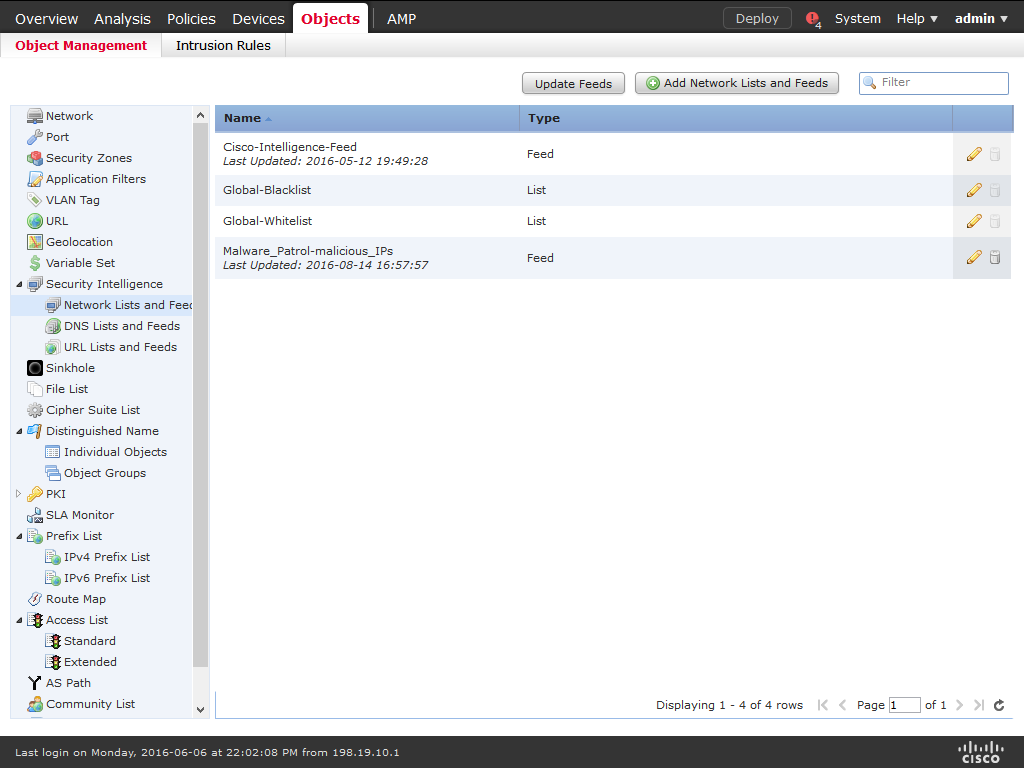
2) Choose Objects > Object Management.
3) Expand the Security Intelligence node, then choose Network Lists and Feeds.
4) Click Add Network Lists and Feeds.
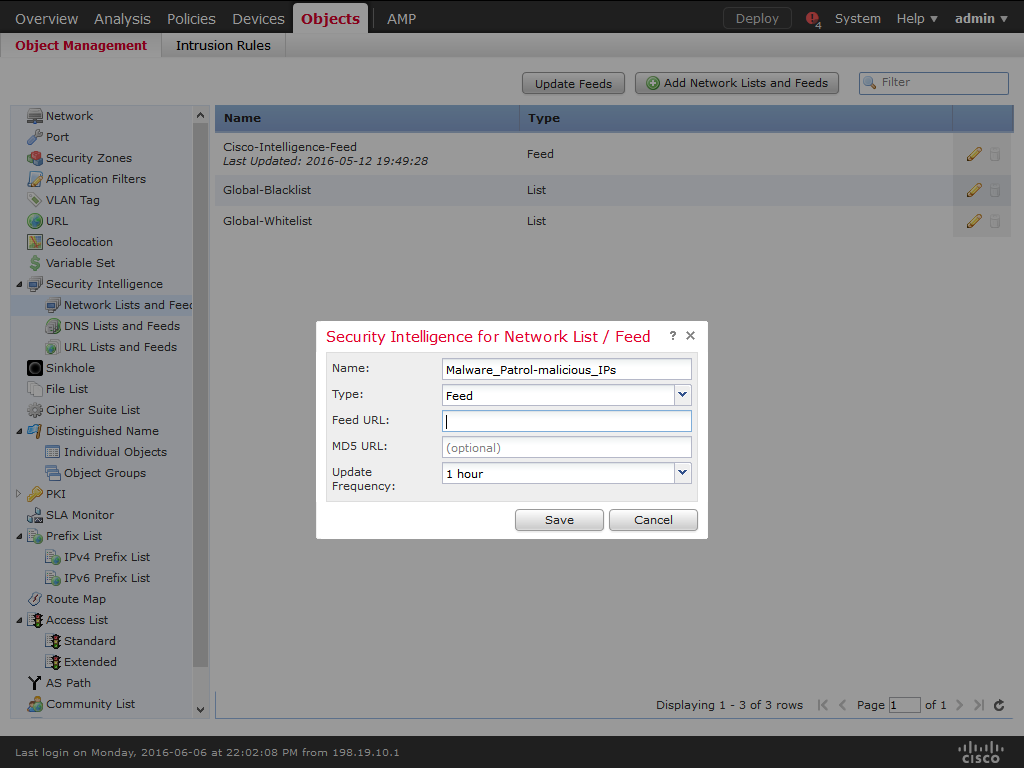
5) Enter a name for the feed (ex: MalwarePatrol_malicious_IPs).
6) Choose Feed from the Type drop-down list.
7) Enter the corresponding feed URL that can be found logging in to the Malware Patrol website.
8) Enter the corresponding feed MD5 URL that can be found logging in to the Malware Patrol website.
9) Choose the Update Frequency, we suggest one hour.
10) Choose Save.
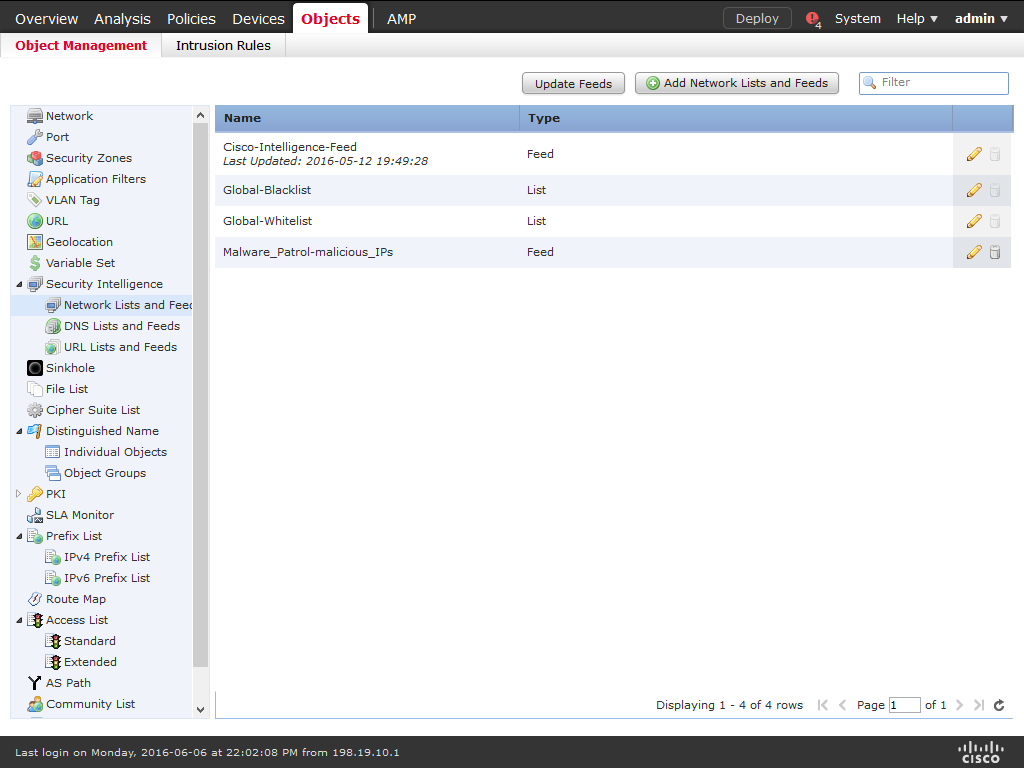
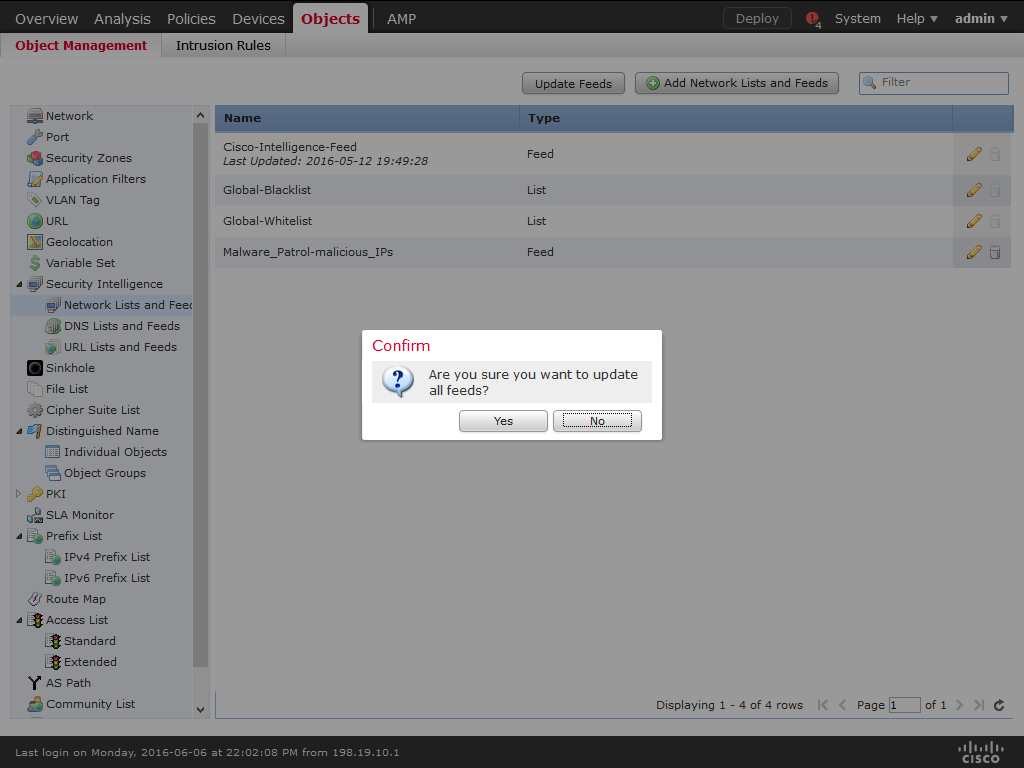
11) Click Update Feeds.
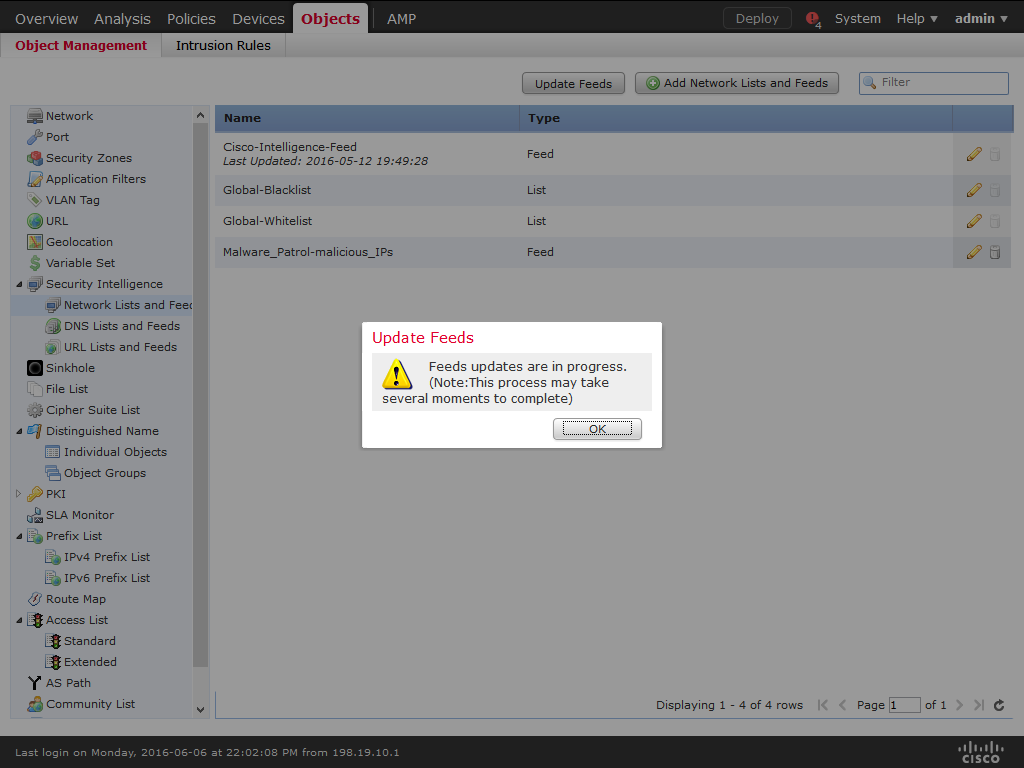
12) Cisco ASA FirePOWER will automatically update the data feed at the chosen interval.
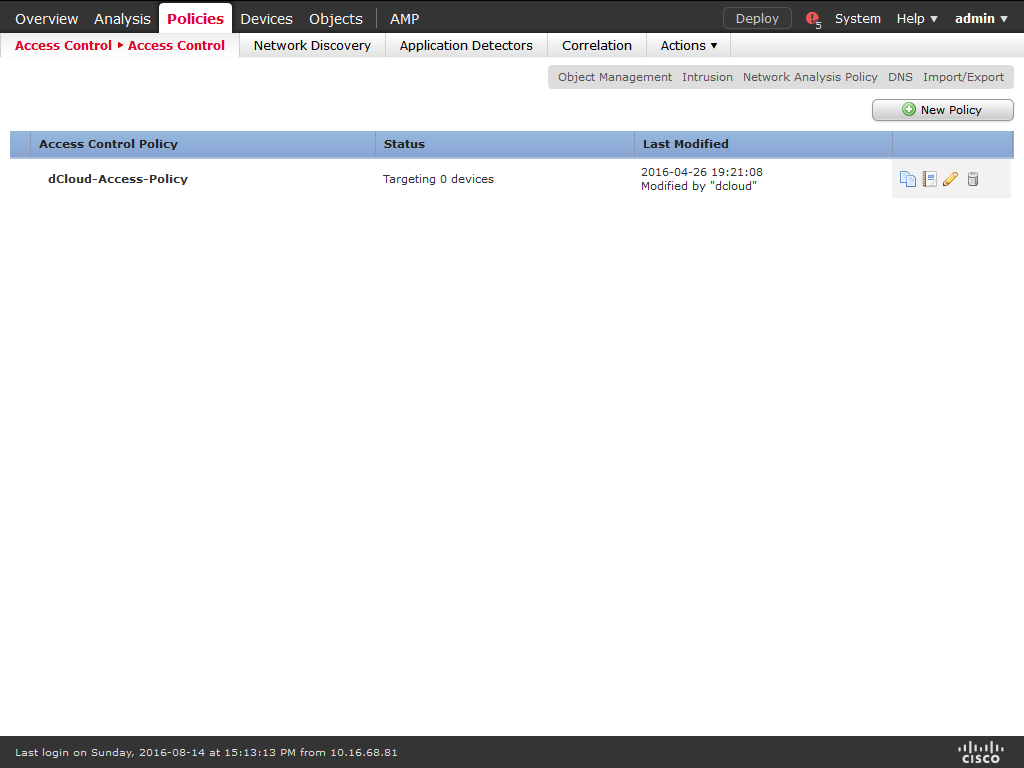
13) Choose Policies / Access Control and click New Policy.
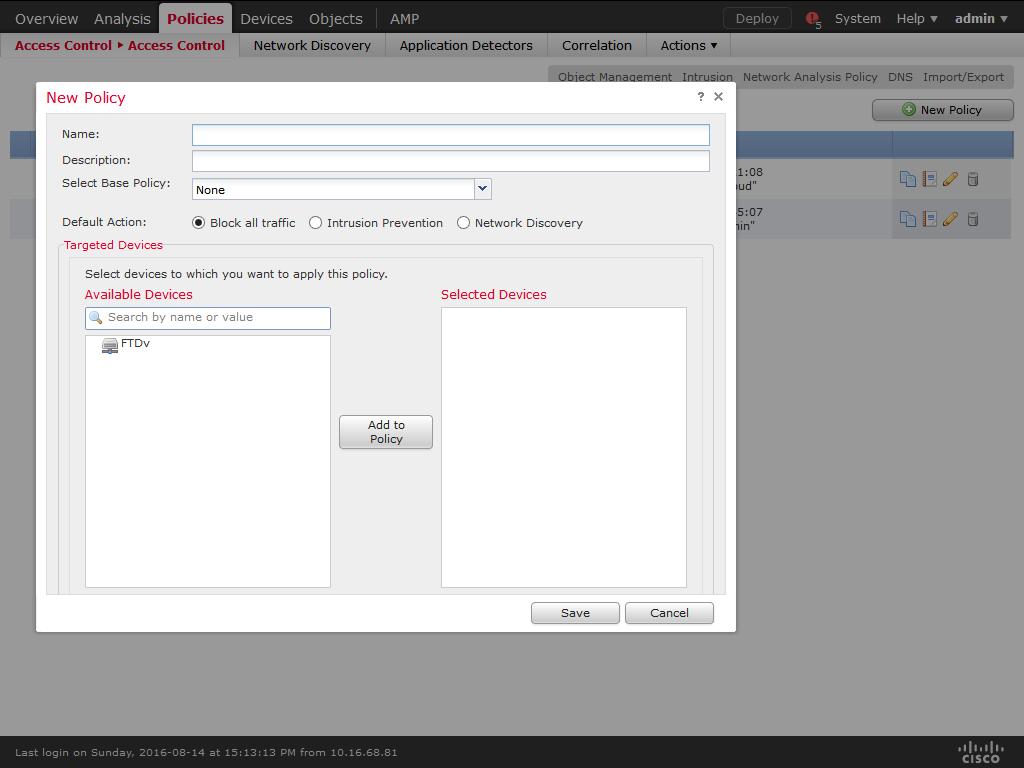
14) Enter a meaningful Name and Description to the policy. The Default Action must be Block all traffic. On Available Devices select the devices that will be affected by the policy and click Add to Policy. When you are done, click Save.
15) A new policy will be created. Click on Security Intelligence.
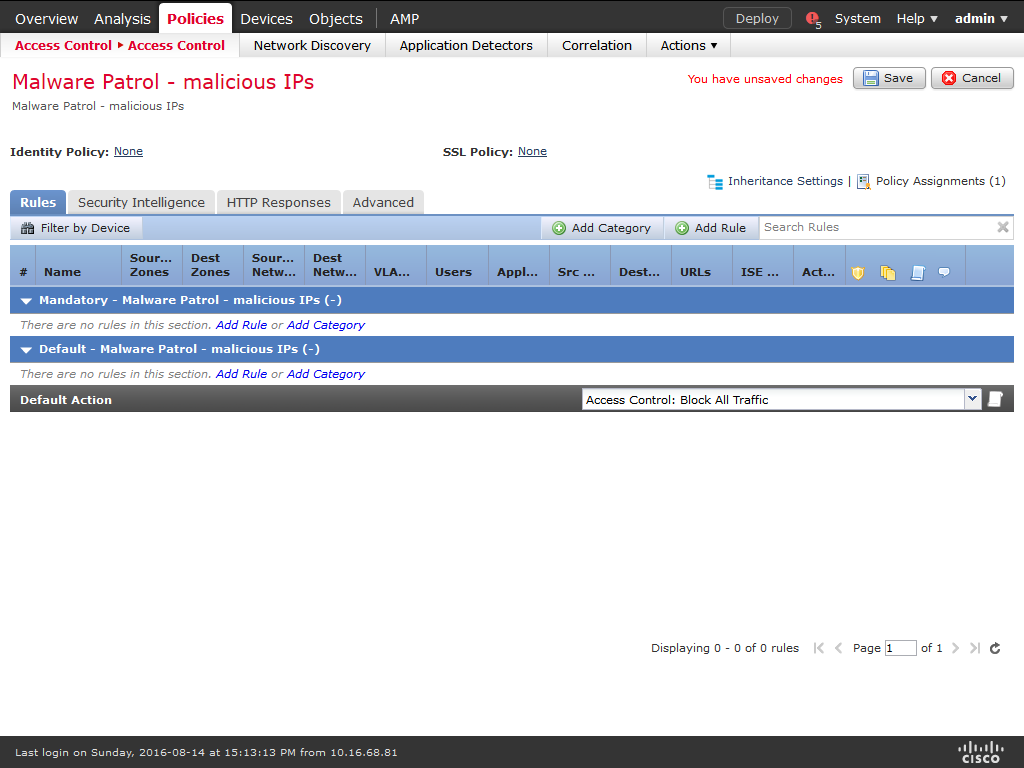
16) On Available Objects / Networks select the object created previously (ex: MalwarePatrol_malicious_IPs), choose a zone from Available zones (Any is the default) and click on Add to Blacklist.
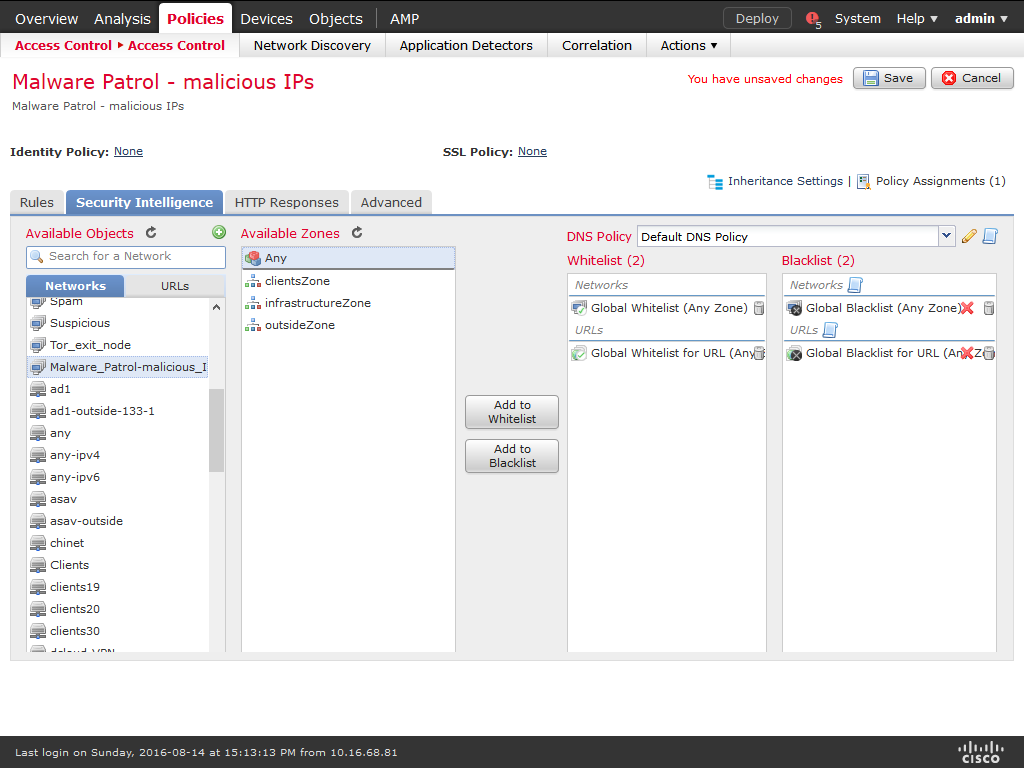
17) The object and corresponding policy were created successfully. You can follow the same steps to use the other data feeds we provide.
If you experience any difficulties configuring Cisco ASA FirePOWER to use Malware Patrol data feeds, please make sure it is working properly and contact our tech support at support (@) malwarepatrol.net.
